Resource Compliancy
This lab covers a basic example workload (using an S3 bucket) in the AWS account created in the previous lab. Select the new AWS account in the AWS Single Sign-On portal.

Workload
To showcase the benefits of a unified AWS environment, you will create an S3 bucket with the default configuration and intentional mistakes. The bucket could - for instance - be used to store internal files or public assets for a static website.
Using this example, a potential workload owner needs to be notified, that an insecure configuration of an AWS resource was applied. Regardless if the configuration is accidental or intended, using superwerker will ensure the same level of security and configuration for AWS resources across your AWS accounts.
Create the S3 bucket
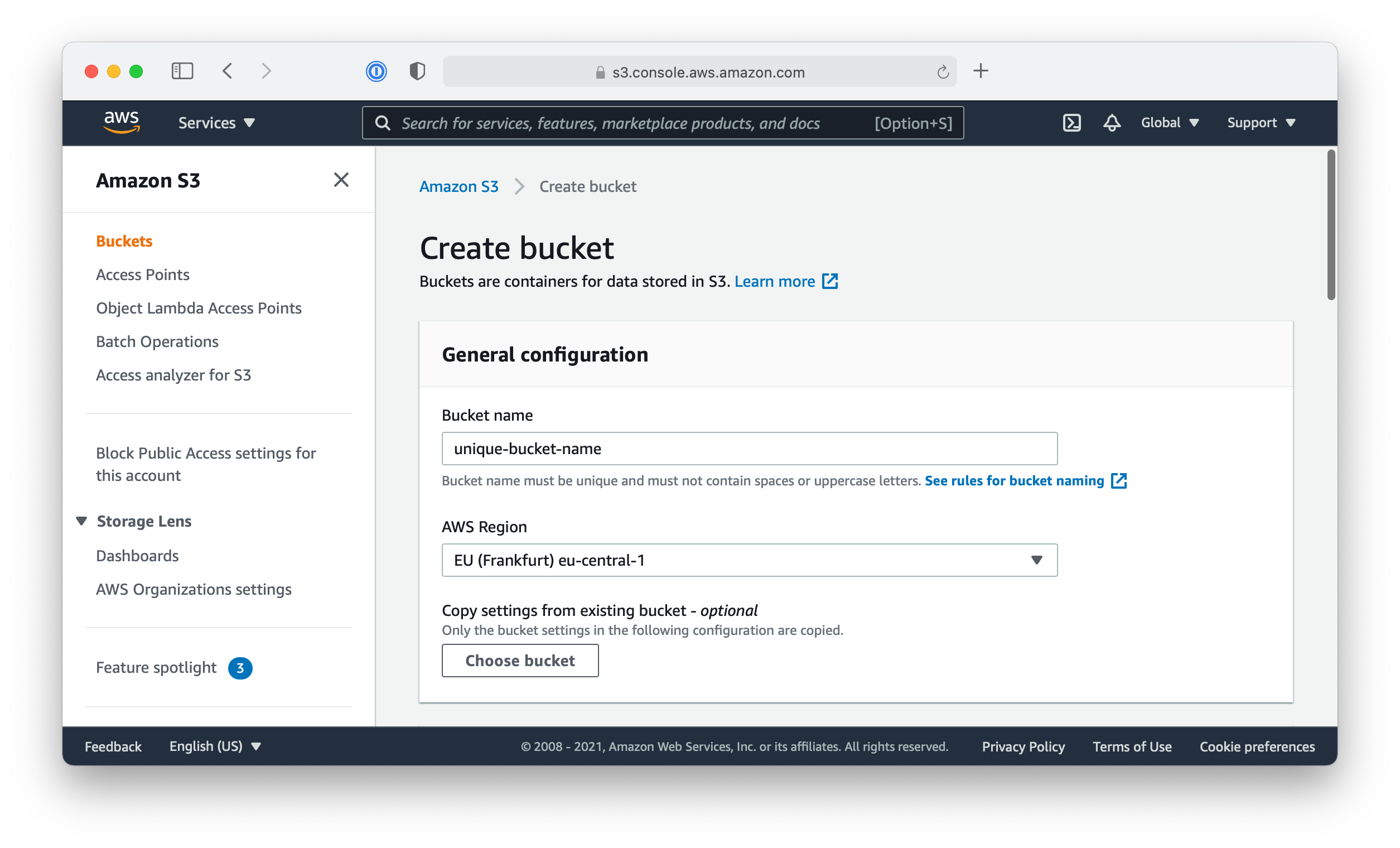
To create a new S3 Bucket, use the AWS S3 console.

- Click the orange “Create bucket” button
- Choose a name and a region for the bucket.
The bucket name needs to be unique (not just in your AWS account) - Keep the default settings for everything else.
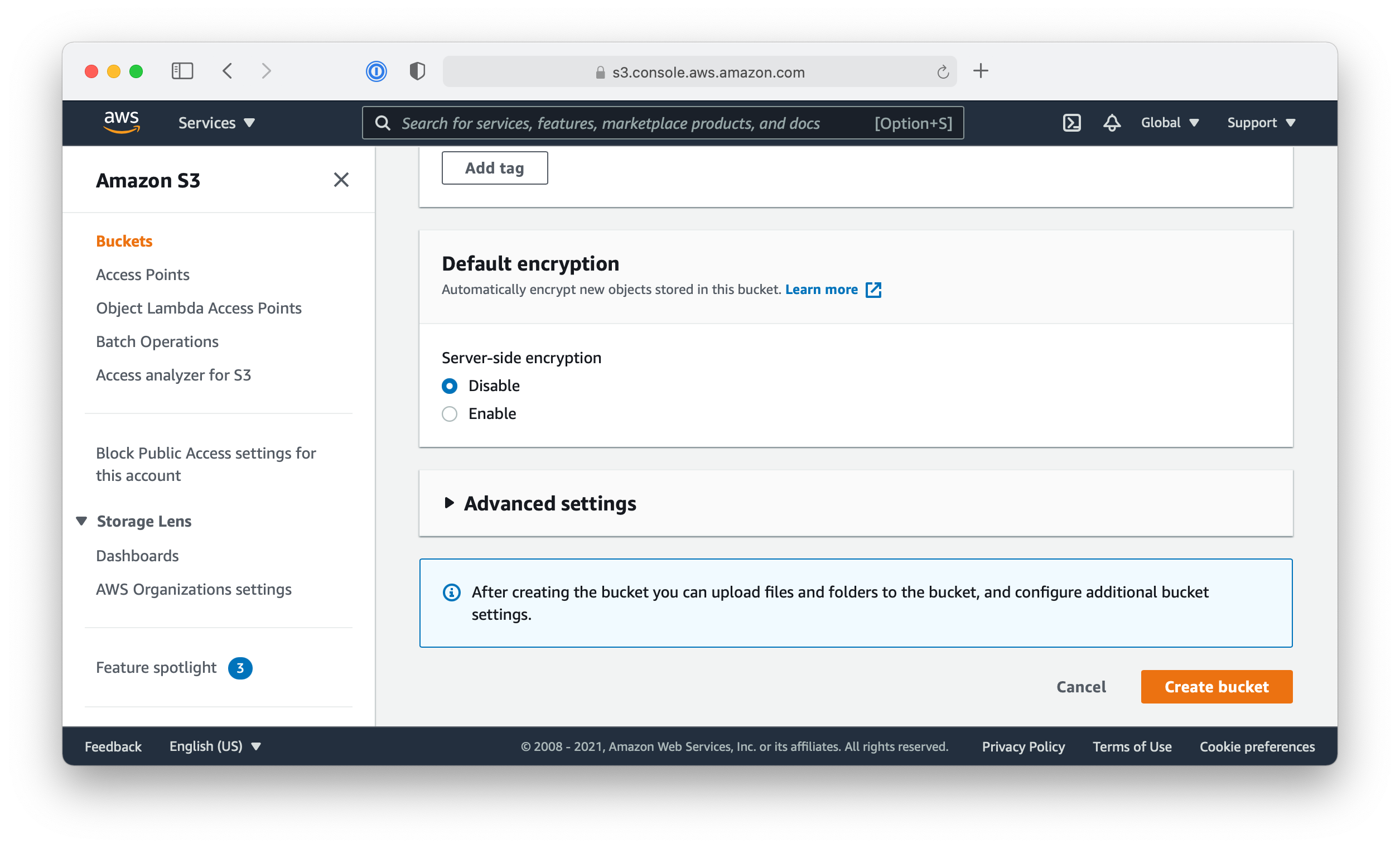
Especially: do not enable “Server-side encryption”. - Create the bucket by clicking the “Create bucket” button
After the S3 bucket was created, you are redirected to the list of your buckets. This list will include the new S3 bucket.
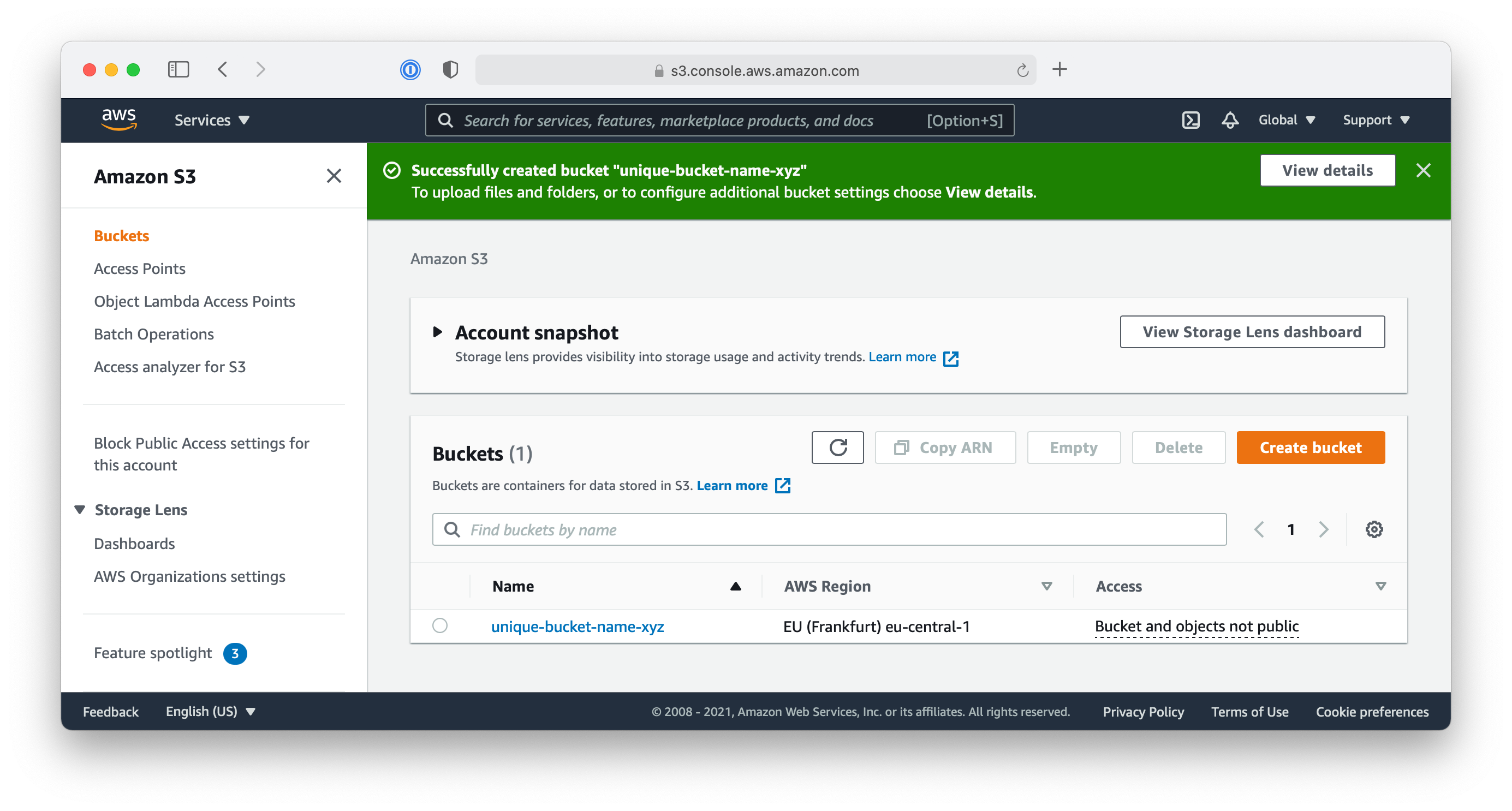
Now that you have created a new S3 bucket without server-side encryption, let’s check if there are any security warnings, that can help us to mitigate this risk.
Security Notification via Security Hub
When using superwerker, AWS Security Hub and AWS Config are enabled to ensure a secure baseline for all resources in your AWS accounts. These services make sure your resources in AWS match the required configuration schema:
- AWS Config checks continuously all AWS resource to match a set of rules
- AWS Security Hub aggregate all security-related notifications in a dashboard
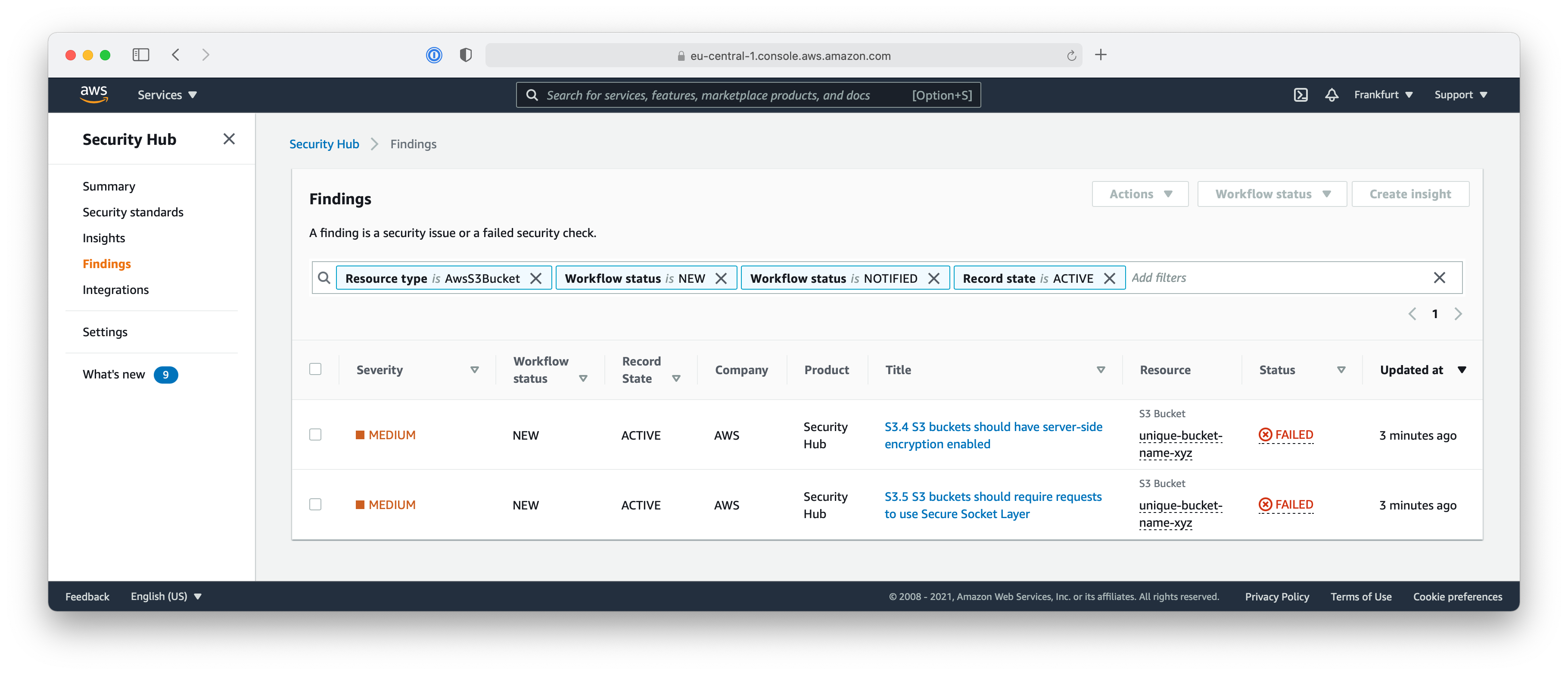
Now you need to check if the misconfiguration (Using unencrypted S3 buckets) was already noticed. To check the current security issues in the workload account use Security Hub service console:
- Select “Findings” from the navigation bar
- Locate the finding related to the new S3 bucket in the list
It might take a couple of minutes until it appears - You can take a closer look at the finding and check out its details view
Update S3 Configuration
Now that you learned where to find notifications for security issues, let’s go ahead and fix the issue.
- Open the AWS S3 console again
- Find your S3 bucket and click on its name to open the details view
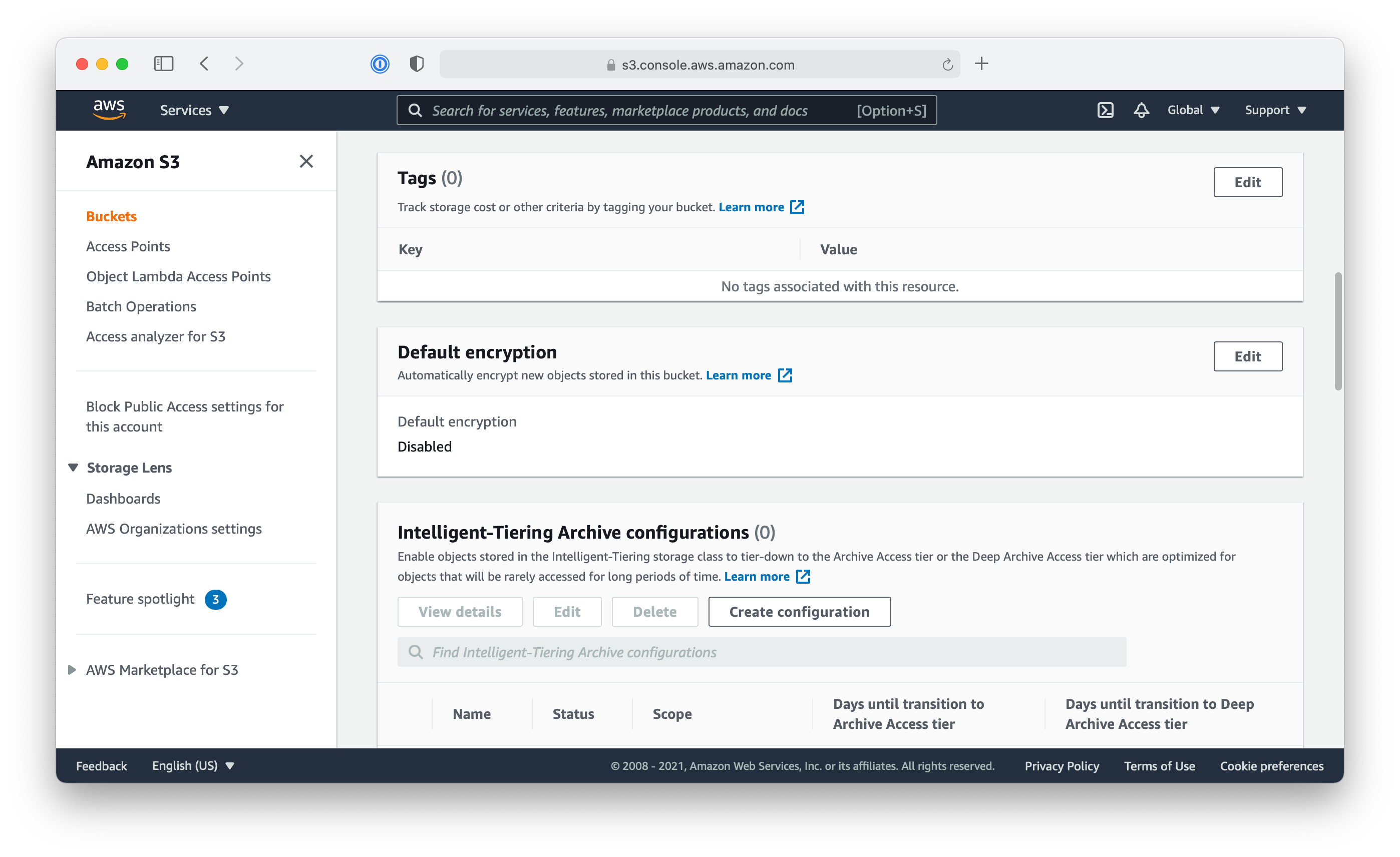
- Click on the “Properties” tab and find the “Default encryption” section
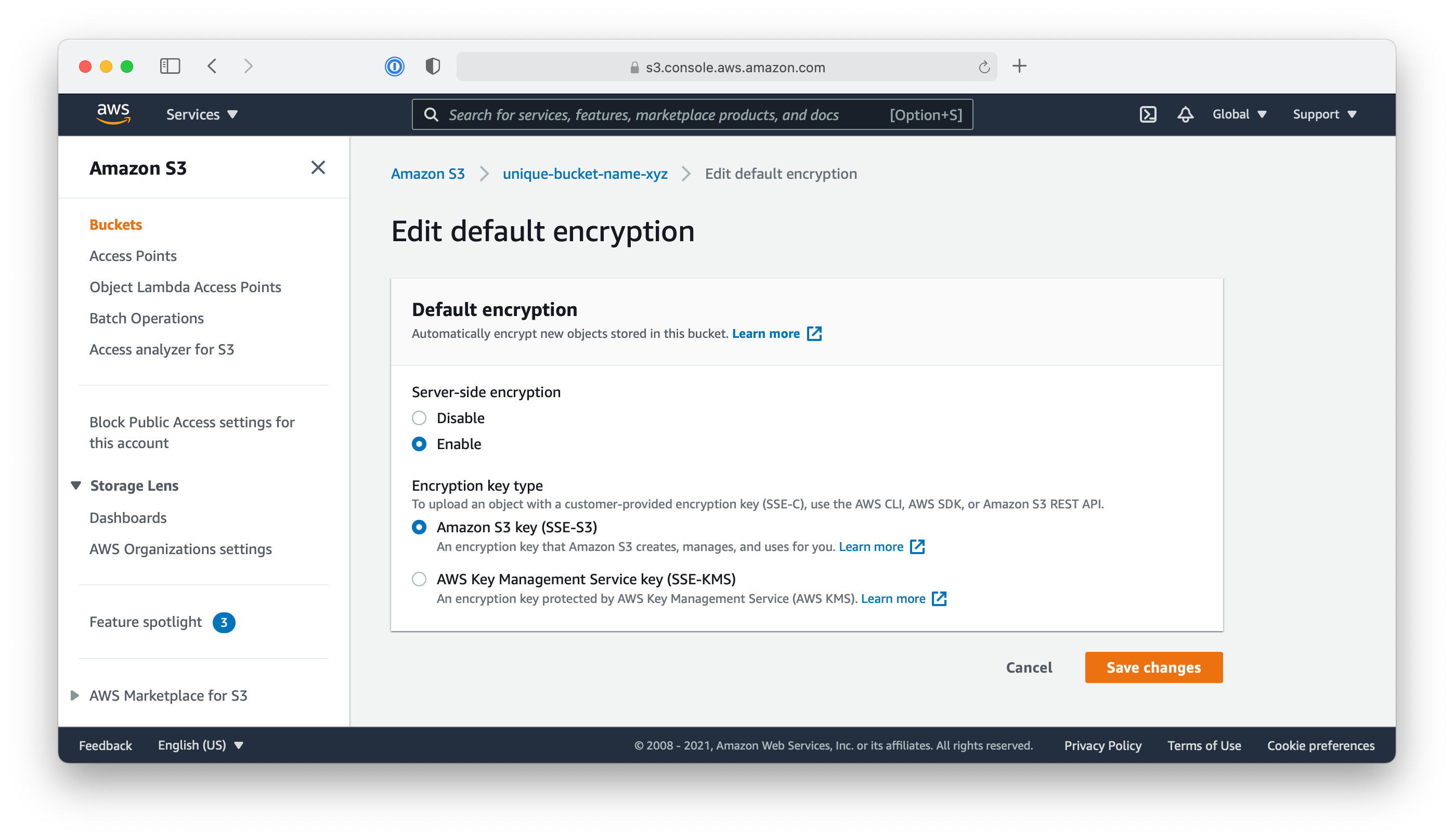
- Click on the “Edit” button and enable the “Server-side encryption”
- Save the changes
Compliance Status in Security Hub
To make sure that the problem is really fixed, you can go back to the Security Hub console and check that the finding no longer shows up.
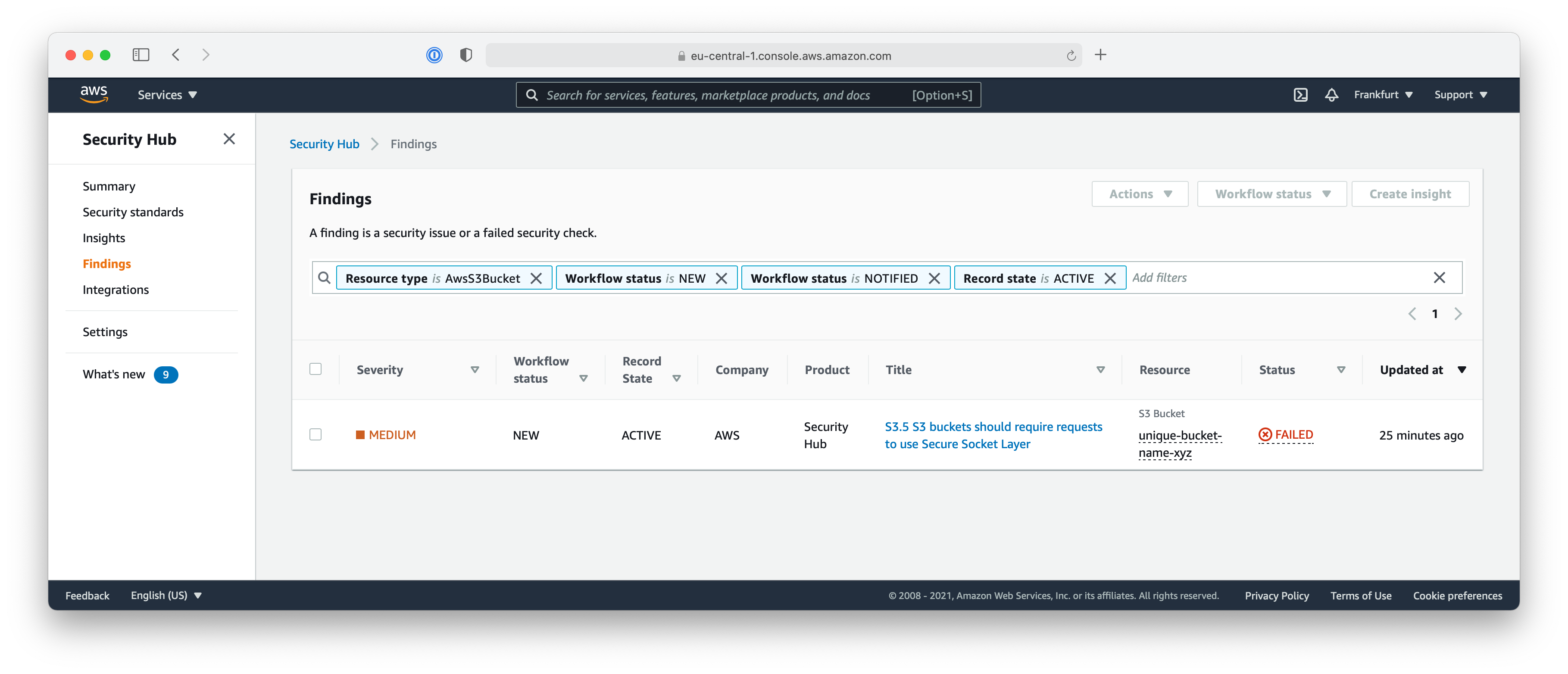
Using the Filters on top of the table of findings, you can change the selection to show passed findings as well and see the status of the finding changed from FAILED to PASSED after you changed the encryption setting.
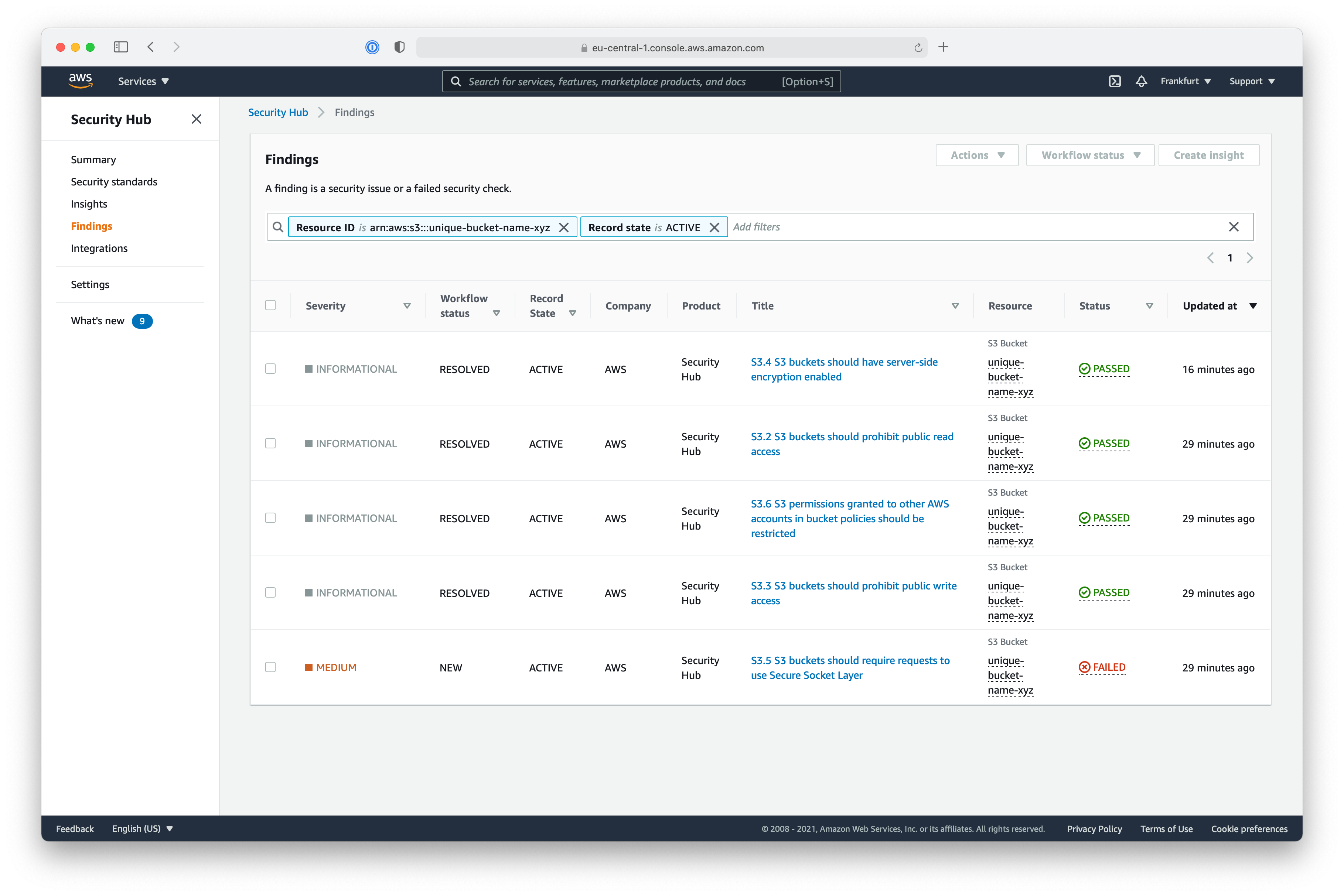
AWS Config
The Security Hub works as an aggregation of findings other services. The unexpected configuration of the S3 Bucket is noticed by a service called AWS Config. You can head over to the service in the AWS Management Console to have a deeper look.

When selecting Resources on the left side, you see all resources in your AWS account monitored by AWS Config. With the filter on top, you can limit it on specific resources types: S3 Buckets for example.
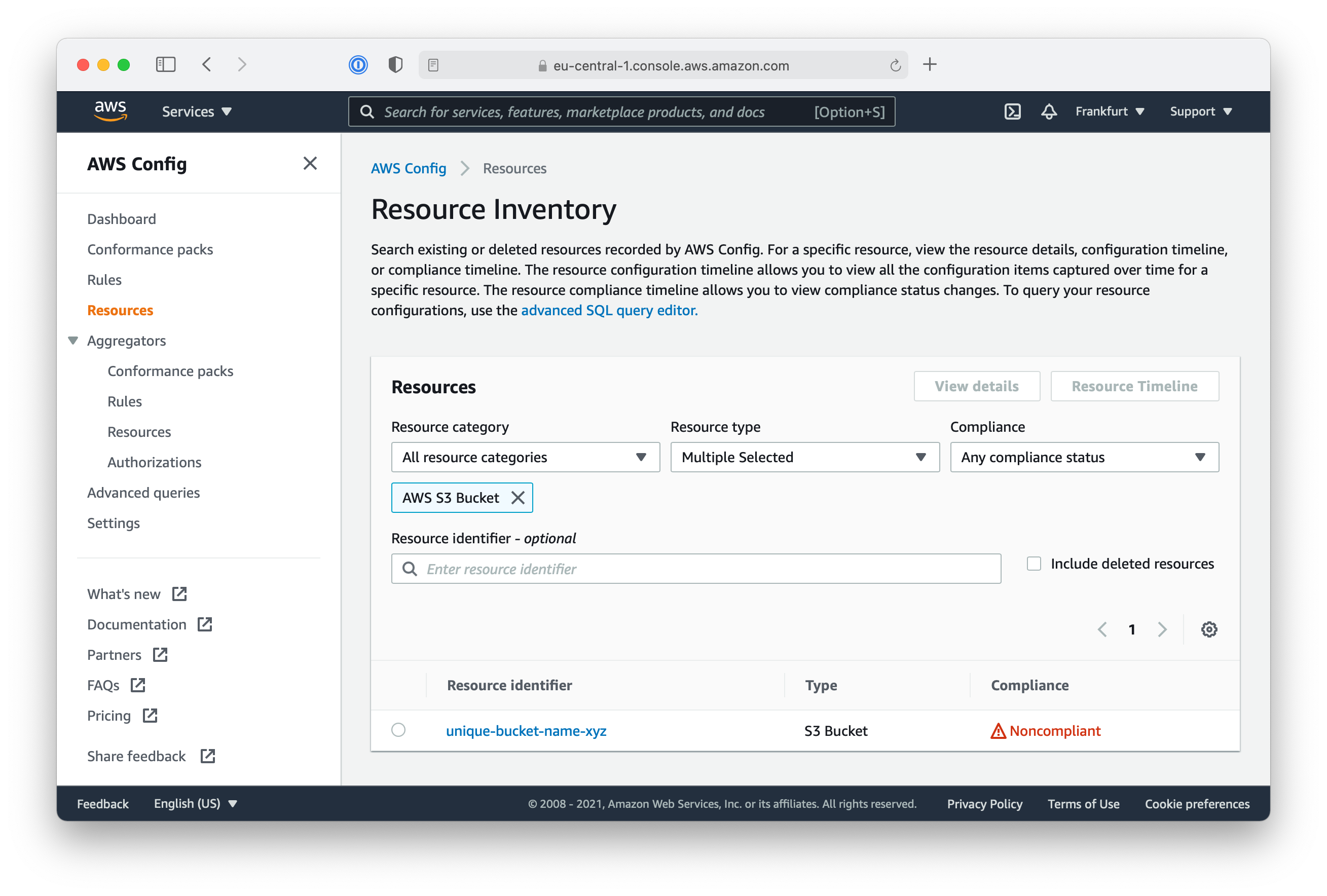
By clicking on a resource name, you are directed to the corresponding details view. Here you’ll find all configuration rules applicable to the type of resource and the current status. As you see, the server-side-encryption-enabled rule is now Compliant.
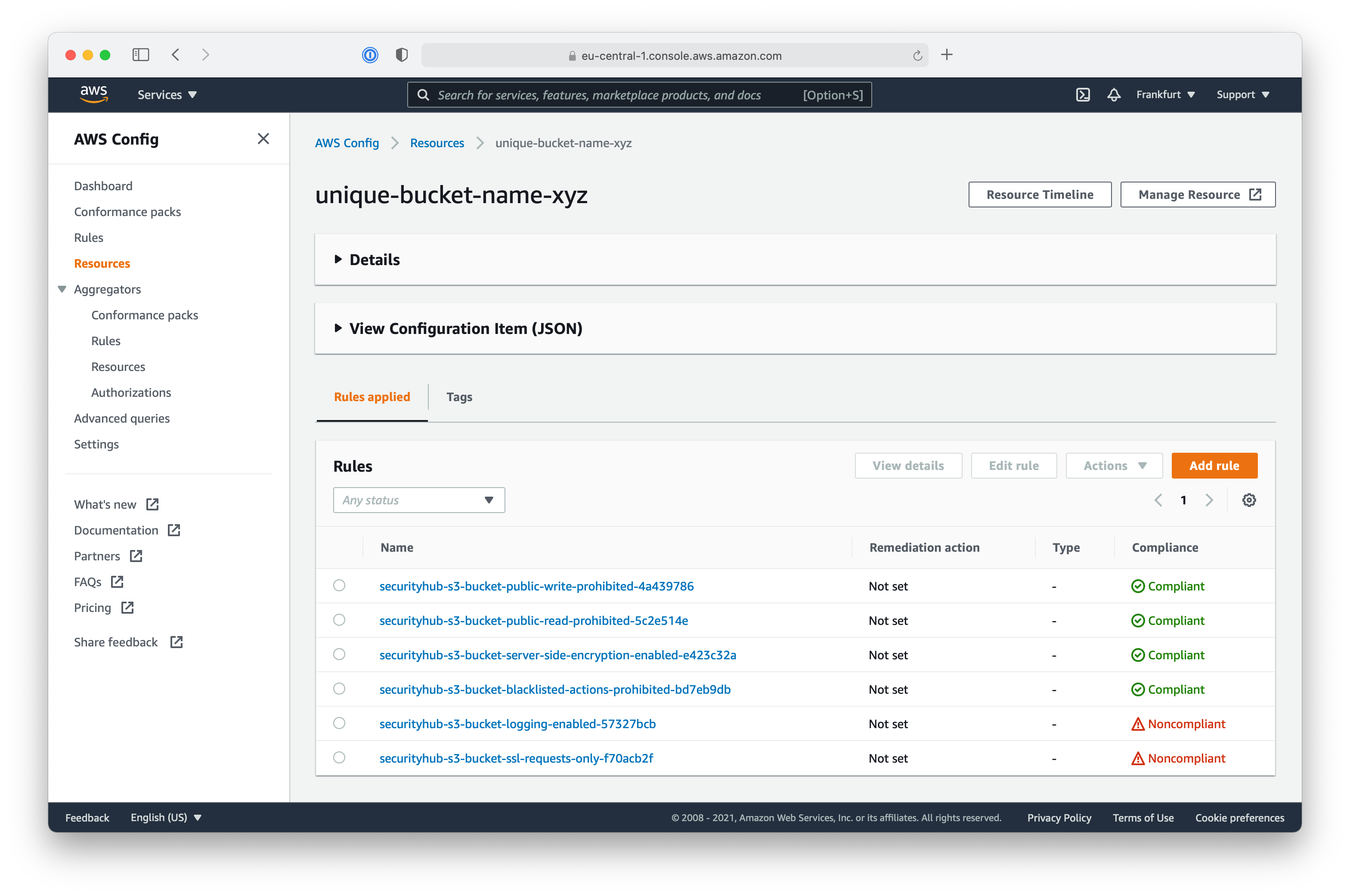
On the details view of the resource, you can access the Resource Timeline to have a deeper look at the events, changes, and compliancy status of a single resource.
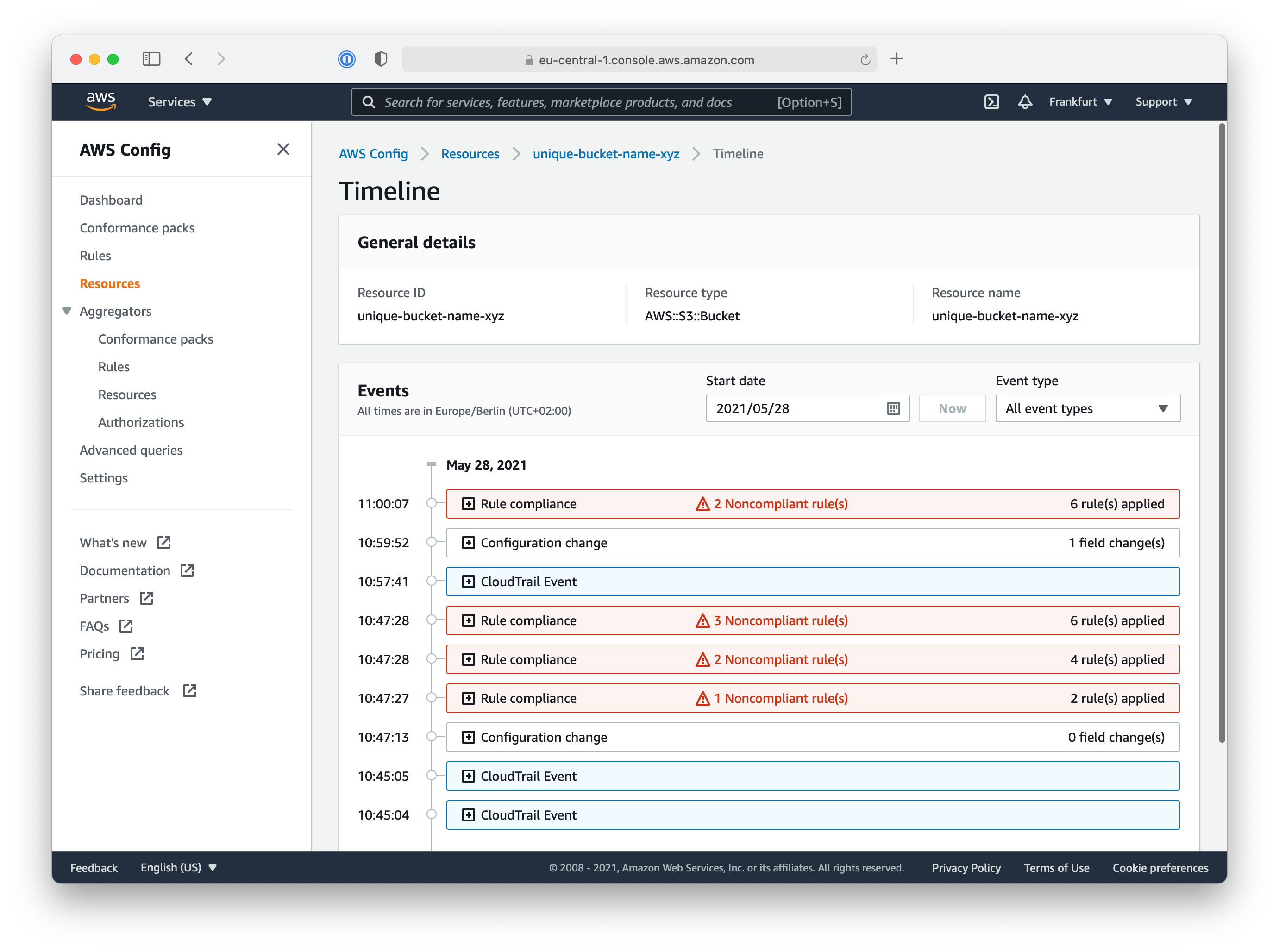
There are still two rules with the status Noncompliant: bucket-ssl-requests-only and bucket-logging-enabled. Can you manage to make your S3 Bucket resource fully compliant with all configuration rules?

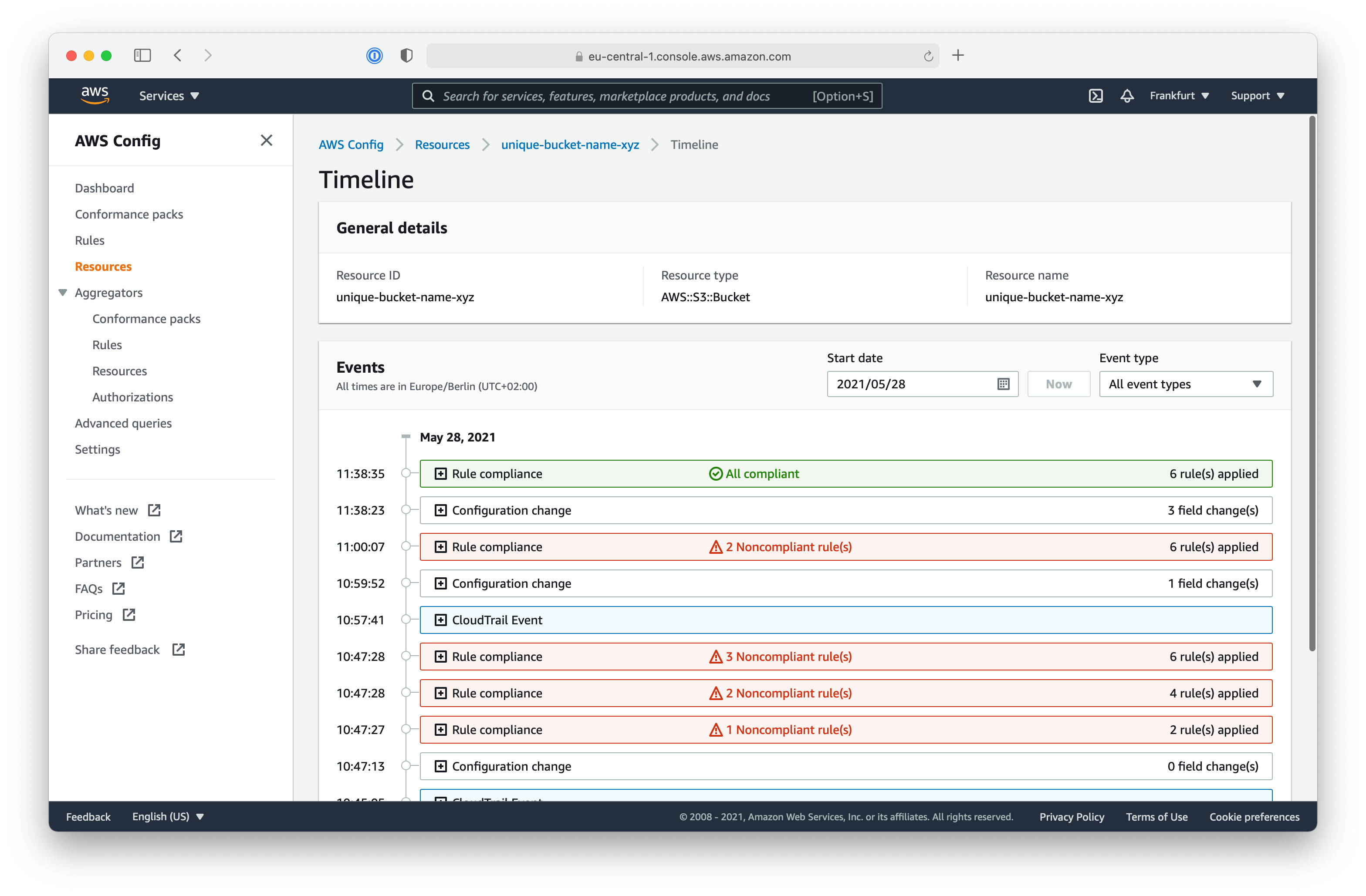
With AWS Config, you can use a variety of managed rules by AWS or even create your own custom AWS Config rules using AWS Lambda.
We looked at our AWS Security Hub notifications to determine if a newly created resource was compliant with rules that superwerker sets in our AWS Config ruleset. We also learned how to use this information to fix security compliance violations that might occur when we provision resources in our AWS accounts. In the next lab we will learn how superwerker keeps our data safe by automatically backing up common storage resources.